Showing posts with label PC Hacking. Show all posts
Tips for Yahoo!
-Avoid P2P file Sharing Through Yahoo! Messenger
-Prefer not to receive any file from your friend unless you know what he is sharing and why. --Avoid downloading .exe or .zip files from them as they are more likely to attack your computer or install trojans or viruses without you know that.
-Never trust a stranger when he asks you to click on any site you haven't heard of.
-Avoid Clicking on Spammy Links:
if you were chatting with someone else and suddenly a PM box flashes on the screen with a lucrative offer/interesting site which has a spammy look, don't click on it. These websites have a lot of spyware who get silently installed if you go and surf them. Never download a toolbar unless its as authenticated as Yahoo!'s or Google's.
-Use Ignore Option Effectively:
Yahoo! has an ignore option that lets you ban a person or mark as spam so that he can't disturb you once again. Use that option effective. Go to Yahoo! Messenger main box -> Preferences -> Ignore List. If you want to avoid talking to strangers (which is always recommend) talk to your buddies only, Check Ignore anyone.. option. That helps you be safe and block on the unwanted and potential hackers from reaching you. See the screen-shot below.
-Use other Chat Clients:
-Use other Chat Clients:
Yahoo! Messenger has too many loopholes. It doesn't have a strong security to block contents either. So, if you want to get rid of spams and porn contents all under one go, then you should go for some popular and secure Yahoo! chat clients like Yazak. You can also go for Yah-Elite and Yam. They may not have the same sophisticated GUI or entertainment features but they will increase the security of the chat sessions by many folds.
-Always Use Newer Versions of Yahoo! Messenger. Remember, the more you stay with the older versions and feel lazy to get upgraded, the more you are helping the hackers. Yahoo! or any software, brings out these updates not only to extend features but also due to security reasons. A newer version of Yahoo! messenger 9 is hardly bootable by DoS attack whereas Yahoo! Messenger 7 can be booted out or hacked by a script kiddie.
-Don't download Yahoo! Plug-ins from Unauthorized Source. Do not ever download a plug-in of Yahoo! messenger from any other site however lucrative it be. Plug-ins like these exploit the vulnerability once installed and send your account details to a third party revealing and cracking down your id. So, better be safe than sorry.
-Use Proxy if you have a Better Firewall Yahoo! also gives you option to change your proxy. Go to Preferences and hunt down Proxy servers. You will see that you can set your own proxy server so that Yahoo! gets redirected through yours giving you a better chance to protect yourself and secure by your network. But if only you have that faith on your network security. You can change it by going to Yahoo! Messenger main box -> Preferences -> Connection
-Use Word Filter. You can also use your word Filter in Yahoo! messenger. It just discards all the obscene or threatening words by intelligent filtering system if you choose Strong option. But be aware, there may be some times when your own friend can get banned while cursing your jokingly. Word filter is another good option to be within your network and not let some specifically targeted spammers to arrive. It increases security too. You can change it by going to Yahoo! Messenger main box -> Preferences -> Chat.
-If you are sharing a public computer to chat from is to change it by going to Yahoo! Messenger main box -> Preferences -> Archive. Change it to No, do not save any of my messages and you are done. Oh don't forget to delete your profile from Profiles inside Yahoo! folder after you sign out.
-Use Word Filter. You can also use your word Filter in Yahoo! messenger. It just discards all the obscene or threatening words by intelligent filtering system if you choose Strong option. But be aware, there may be some times when your own friend can get banned while cursing your jokingly. Word filter is another good option to be within your network and not let some specifically targeted spammers to arrive. It increases security too. You can change it by going to Yahoo! Messenger main box -> Preferences -> Chat.
-If you are sharing a public computer to chat from is to change it by going to Yahoo! Messenger main box -> Preferences -> Archive. Change it to No, do not save any of my messages and you are done. Oh don't forget to delete your profile from Profiles inside Yahoo! folder after you sign out.
-Apply Your Common sense and Use a good Antivirus and anti Spyware software. Applying your common sense is the least you can do to prevent your account from being hacked. A good anti-virus and anti-spyware always warns you about dangers that you may have overlooked. So its better to have them as well. If you implement the above tips, you won't need to worry much. I gues until you personally hand over your information to the person willing to crack your computer down.
How To Rename Your Recycle Bin
1. Click Start / Run
2. Type regedit and press enter.
3. Open the HKEY_CLASSES_ROOT folder
4. Open the CLSID folder
5. Open the {645FF040-5081-101B-9F08-00AA002F954E} folder
6. Open the ShellFolder folder
7. Change the "Attributes" data value from "40 01 00 20" to "50 01 00 20". Once completed change the "CallForAttributes" dword value to "0x00000000" (doubleclick and change value data to 0). You must change both of these values to get the rename to appear.
After performing the above steps you will be able to rename the icon like any other icon. Right-click the Recycle Bin icon on the desktop and click Rename and rename it to whatever you wish.
How to hide files in a .jpg
Set up:
1. You must have a .zip or .rar compressor.
Steps:
1. Save the picture of choice to your desktop.
2. Make a new .rar or .zip folder on your desktop.
3. Add the files you want to hide into the .zip or .rar
4. Click start menu, run, cmd.
5. In Command Prompt type cd "desktop" with the quotation marks.
6. Now type in copy /b picturename.jpg + foldername.rar outputfilename.jpg
( If you use .zip then: copy /b picturename.jpg + foldername.zip outputfilename.jpg)
7. Now there should be the outputed file name with a .jpg extension on the desktop. ( Do not close Command Prompt just yet )
8. Double click it to open the picture and check it out.
9. When your done looking, and want to view the hidden files Type: ren outputfilename.jpg outputfilename.rar or .zip
Now you're done!
A quick info-fact:
With this technique of hiding files in a jpg you can send this to anyone and they just have to rename the file extension to .zip or .rar.
With this technique the Al-Qaeda operatives were able to send info to others secretively.
How to make Folder Lock Without Any Software
Folder Lock With Password Without Any Software-
Paste the code given below in notepad and 'Save' it as batch file (with extension '.bat'). Any name will do.
Then you see a batch file. Double click on this batch file to create a folder locker. New folder named 'Locker' would be formed at the same location.
Now bring all the files you want to hide in the 'Locker' folder. Double click on the batch file to lock the folder namely 'Locker'.
If you want to unlock your files,double click the batch file again and you would be prompted for password.
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N) set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" attrib +h +s "Control Panel.{21EC2020-3AEA-1069-
A2DD-08002B30309D}"
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder set/p "pass=>"
if NOT %pass%==type your password here goto FAIL attrib -h -s "Control Panel.{21EC2020-3AEA-1069-
A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" Locker echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
How to make Mozilla Firefox 30 times faster
Type "about:config" into the address bar and hit return. Scroll
down and look for the following entries:
down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
Normally the browser will make one request to a web page at a time. When you enable pipelining it will make several at once, which really speeds up page loading.
Alter the entries as follows:
Set "network.http.pipelining" to "true"
Set "network.http.proxy.pipelining" to "true"
Set "network.http.pipelining.maxrequests" to some number like 30. This means it will make 30 requests at once.
Lastly right-click anywhere and select New-> Integer.
Name it "nglayout.initialpaint.delay" and set its value to "0".
This value is the amount of time the browser waits before it acts on information it recieves.
How to hack an Administrator account with a guest account
-The only way this is going to work is if your account has permission to mody files in folder «system32»
Ever wanted to hack your college pc with guest account so that you can download with full speed Hack Administrator? Or just wanted to hack your friend’s pc to make him gawk when you tell your success story of hacking ? Well,there is a great way of hacking an administrator account from a guest account by which you can reset the administrator password and getting all the privilages an administrator enjoys on windows.
To make this press shift key 5 times and the sticky key dialog shows up.This works even at the
logon screen. But If we replace the sethc.exe which is responsible for the sticky key
dialog,with cmd.exe, and then call sethc.exe by pressing shift key 5 times at logon
screen,we will get a command prompt with administrator privilages because no user
has logged on. From there we can hack the administrator password,even from a guest
account.
Guest account with write access to system 32. Here is how to do that -
Go to C:/windows/system32
Copy cmd.exe and paste it on desktop
rename cmd.exe to sethc.exe
Copy the new sethc.exe to system 32,when windows asks for overwriting the file,then click yes.
When asked to overwrite, overwrite the sethc.exe.
Now Log out from your guest account and at the user select window,press shift key 5 times.
Instead of Sticky Key confirmation dialog,command prompt with full administrator privileges will open.
Press shift key 5 times and command prompt will open.
Now type “ NET USER ADMINISTRATOR xxxx” where “xxxx” can be any password you like and press enter.
You will see “ The Command completed successfully” and then exit the command prompt and login into administrator with your new password.
Congrats You have hacked admin from guest account.
Also, you can further create a new user at the command prompt by typing “NET USER Ephemeral /ADD” where “Ephemeral” is the username you would like to add with
administrator privileges. Then hide your newly created admin account by -
Go to registry editor and navigate to this key
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\Winlogon\SpecialAccounts\UserList]
Here create a new DWORD value, write its name as the “user name” that u created for your admin account and live with your admin account forever :)
How to get unlimited time in internet cafe's
Hello, now we're going to learn how to disable the timer on the computers in Internet Cafe's.
Let's go through the steps:
1. Create a New Text Document.
2. Then type CMD in it.
3. And then save it as anything.bat
(Make sure the file do NOT end on .txt, but on .bat)
4. Go to the location were you saved the .bat file and run it. If you've done this correctly, you'll see that Command Prompt is open.
5. Now that Command Prompt is open, type in: cd\windows (This will change the directory to Windows)
6. Then type in: regedit
(This will get you to the registry editor gui)
7. Now navigate to:
HKEY_CURRENT_USER>Appevents>software>classes>microsoft>windows>current version>internet settings>policies>system
8. Then on the right pane where it says Disable Taskmanager, right click on it, and scroll down to modify, and than change the value of it to "0".
9. And then open Windows Task Manager
(CTRL+ALT+DELETE) (CTRL+SHIFT+ESCAPE !win 7)
10. And then disable the Internet Cafe's timer.
How to use trail program forever
How to use a trial program forever without activation
In this post I’ll show you how to “hack” a Software and run the trial program forever. Most of us are familiar with many software's that run only for a specified period of time in the trial mode. Once the trial period is expired these software's stop
functioning and demand for a purchase. But there is a way to run the software's and make them function beyond the trial period. Isn’t this interesting?
functioning and demand for a purchase. But there is a way to run the software's and make them function beyond the trial period. Isn’t this interesting?
Before I tell you how to “hack” the software and make it run in the trial mode
forever, we have to understand the functioning of these software's. I’ll try to explain this in brief.
When these software's are installed for the first time, they make an entry into the Windows Registry with the details such as Installed Date and Time, installed path etc. After installation every time you run the software, it compares the current system date and time with the installed date and time. So, with this it can make out whether the trial period is expired or not.
So with this being the case, just manually changing the system date to an earlier date
will not solve the problem. For this purpose there is a small Tool known as RunAsDate.
will not solve the problem. For this purpose there is a small Tool known as RunAsDate.
RunAsDate is a small utility that allows you to run a program in the date and time that you specify. This utility doesn’t change the current system date, but it only injects the date/time that you specify into the desired application.
RunAsDate intercepts the kernel API calls that returns the current date and time (GetSystemTime, GetLocalTime, GetSystemTimeAsFileTime), and replaces the current date/time with the date/time that you specify.
It works with Windows 2000, XP, 2003 and Vista.
Follow this tips carefully
You have to follow these tips carefully to successfully “hack” a software and make it run in it’s trial mode forever.
1. Note down the date and time, when you install the software for the first time.
2. Once the trial period expires, you must always run the software using RunAsDate.
3. After the trial period is expired, do not run the software(program) directly. If you run the software directly even once, this “hack” may no longer work.
4. It is better and safe to inject the date of the last day in the trial period.
For example, if the trial period expires on jan 30 2009, always inject the date as jan 29 2009 in the RunAsDate.
Here you can download RunAsDate:
How to kick everyone from counter strike server
INSTRUCTIONS:
1. Place Buffer1.cfg and Buffer2.cfg in your cfg folder. If it doesn't exist, make it (see below)
(Commonly C:\User\program files\steam\steamapps\Account name\counter-strike source\cstrike\cfg)
2. Go in game, open the developer's console, and type in the following (you may change bind key):
Bind M "wait;exec Buffer1;exec Buffer2"
(If developer's console doesn't open, go to options, keyboard, advanced, enable developer's console)
3. Go in game and rapidly hit the M key to crash the server. Depending on how fast you hit it, it should
take anywhere from 15-30 seconds to crash. Don't stop hitting the key until you get a message:
"Client # has overflowed reliable channel."
Download Buffers:
How to find the “real” IP address of a web site?
You can use the PING utility included with Windows to determine the “real” IP address of a web site. Before using this utility, make sure you are not mapping a host name to some IP address with HostName Commander, because if you do, the PING utility will show the address you’ve set up with HostName Commander, instead of the “real” IP address.
To run the PING utility, click on the Windows Start button, and choose Run from the Start Menu. If you use Windows 95,98, or Me, enter “command” (without the quotes) as the command line to run. If you use Windows XP,2000, or NT, enter “cmd” (again, without the quotes). Click OK and the command prompt window should appear on the screen.
Now enter the word “ping” (without the quotes) followed by a space, followed by the host name you want to determine the IP address of, and press Enter:

In this example, the IP address of the host name www.rkgit.edu.in is 74.52.201.2 & IP Address of the host name www.kiet.edu is 220.225.19.55 . (Keep in mind that the IP address may change in the future!). If the PING utility reports an error, make sure your computer is connected to the Internet when you are running it.
Hack Facebook account
1. Download the keylogger and Extract the files. Download
2. Now Enter the Details of fake gmail account that you have to create to use it.(for security reasons)
3. Now Set the timer to receive logs to your email address.
4. Now click on send verification to check whether the Keylogger is working correctly or not.
5. Now Go to mutex text column. There type anything waste (note try to include as many as special characters as possible and atleast 70 to 80 characters). Don't click on Generate.
6. Now click on Compile Server to Create the Keylogger. It will ask you to save the file. Select desktop to save the file and name it whatever you want.
Now you have keylogger's server created. Now for binding and make it undetectable and spreading it online then visit to this post:
Hello friends today i will explain you how to hack the Facebook password or accounts remotely using keylogger. Its a 100% working hack and you can easily hack anyone's Facebook account or password using this hack. In this tutorial i will explain you how to hack Facebook and other passwords of any user using 100% FUDkeylogger. The keylogger in this tutorial we will discuss is L33ts keylogger adn its 100% FUD(fully undetectable).
Hacking Facebook account is very easy and just requires not more than 10 minutes of work. Don't worry i will also tell you how to protect your facebook account or passwords from such hacks and hackers. But for this you must know how hackers hack your facebook account. So first i teach you how to hack facebook account remotely and then i will tell how to protect yourself from this.
Step 1:
Step 1. Creating the Keylogger Server
2. Extract the file, Now you will get two folders:
a. First one contains Keylogger and Binder
b. Second Contains resource hacker tool.( to extract the icons from installers).
3. Now open the Keylogger. It contains two files one for gmail email and other for password. For this create one test account on Gmail and enter it's details in this.
4. After entering email and password. Set the time interval usually set 3 mins i.e. after how much time you want to receive logs from the user.
5. Now click on send verification mail. This mail is to test that your keylogger is working correctly or not.
6. After you click this you will receive a confirmation mail on test account which will confirm that keylogger is working.
7. Now click on generate to set the mutex (any secret key to make your keylogger FUD) and then click on compile server.
8. Now save the file to desktop or any other location of your choice. Now your server is ready but it can be easily detected.
Step 2.: Extracting the Icon file from any installer(resource hacker)
1. Open the Resource hacker folder and open the reshacker file.
2. Now go to its menu and open any setup file. Suppose we want to attach our keylogger to Ccleaner setup file. So open the Ccleaner setup with resource hacker.
3. Now in menu there is one action button click on it and then click save all resources.
4. Now save all the resources to desktop or any other location of your choice.
5. It consists of two files one is icon file and other is res file . We only need icon file, so you can delete the other file i.e res file.
6. Now we have Icon of installer file(as discussed above Ccleaner setup Icon).
Step 3: Bind the Keylogger server with any software
1. Now Go to keylogger folder and open the Binder.
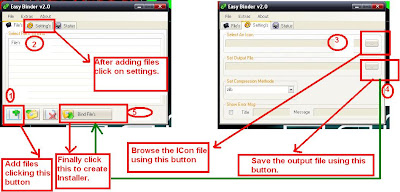
2. Now Click on + button given below to add files.
3. Now add the keylogger server and the set up of software (i.e. in our case it's Ccleaner setup).
4. Now in menu of Binder, Go to Settings. There select the icon that we have generated in the previous step and set the location of output file as shown in figure.
5. Now again go to File's menu in Binder and click on Bind files.
6. Now your Binded keylogger is ready. Now you have to spread it or send it to the victim that is your friend.
Step4 : How to Spread Keylogger or send it to victim or friend
1. Now you have one Software setup file with keylogger attached with it.(In our case we have Ccleaner setup with keylogger attached with it.
2. Now Spread your keylogger through forums. You might be a member of various forums use them to spread your keylogger in form of software posts. You can use various software's to spread them that users frequently download.
3. Spread it through pendrives or USB hard drives. Suppose a friend asked you for a software give it the software that has keylogger attached with it.
Note: you can also attach keylogger with images also. But that can be detectable by antivirus. So avoid such type of hacking.
So isn't that so easy to hack anyone's Facebook account in just few minutes.
How to protect yourself from these hacks?
Prevention is always better than cure so always follow these steps:
1. Don't use cracked softwares and don't download them from unauthorized websites.
2. Always keep your antivirus and anti-spyware up to date.
3. Always scan the files before transferring them to your USB.
4. Do not allow other users to use your PC i.e password protect it.
Hacking Facebook account is very easy and just requires not more than 10 minutes of work. Don't worry i will also tell you how to protect your facebook account or passwords from such hacks and hackers. But for this you must know how hackers hack your facebook account. So first i teach you how to hack facebook account remotely and then i will tell how to protect yourself from this.
Step 1. Creating the Keylogger Server
2. Extract the file, Now you will get two folders:
a. First one contains Keylogger and Binder
b. Second Contains resource hacker tool.( to extract the icons from installers).
3. Now open the Keylogger. It contains two files one for gmail email and other for password. For this create one test account on Gmail and enter it's details in this.
4. After entering email and password. Set the time interval usually set 3 mins i.e. after how much time you want to receive logs from the user.
5. Now click on send verification mail. This mail is to test that your keylogger is working correctly or not.
6. After you click this you will receive a confirmation mail on test account which will confirm that keylogger is working.
7. Now click on generate to set the mutex (any secret key to make your keylogger FUD) and then click on compile server.
8. Now save the file to desktop or any other location of your choice. Now your server is ready but it can be easily detected.
Step 2.: Extracting the Icon file from any installer(resource hacker)
1. Open the Resource hacker folder and open the reshacker file.
2. Now go to its menu and open any setup file. Suppose we want to attach our keylogger to Ccleaner setup file. So open the Ccleaner setup with resource hacker.
3. Now in menu there is one action button click on it and then click save all resources.
4. Now save all the resources to desktop or any other location of your choice.
5. It consists of two files one is icon file and other is res file . We only need icon file, so you can delete the other file i.e res file.
6. Now we have Icon of installer file(as discussed above Ccleaner setup Icon).
Step 3: Bind the Keylogger server with any software
1. Now Go to keylogger folder and open the Binder.
2. Now Click on + button given below to add files.
3. Now add the keylogger server and the set up of software (i.e. in our case it's Ccleaner setup).
4. Now in menu of Binder, Go to Settings. There select the icon that we have generated in the previous step and set the location of output file as shown in figure.
5. Now again go to File's menu in Binder and click on Bind files.
6. Now your Binded keylogger is ready. Now you have to spread it or send it to the victim that is your friend.
Step4 : How to Spread Keylogger or send it to victim or friend
1. Now you have one Software setup file with keylogger attached with it.(In our case we have Ccleaner setup with keylogger attached with it.
2. Now Spread your keylogger through forums. You might be a member of various forums use them to spread your keylogger in form of software posts. You can use various software's to spread them that users frequently download.
3. Spread it through pendrives or USB hard drives. Suppose a friend asked you for a software give it the software that has keylogger attached with it.
Note: you can also attach keylogger with images also. But that can be detectable by antivirus. So avoid such type of hacking.
So isn't that so easy to hack anyone's Facebook account in just few minutes.
How to protect yourself from these hacks?
Prevention is always better than cure so always follow these steps:
1. Don't use cracked softwares and don't download them from unauthorized websites.
2. Always keep your antivirus and anti-spyware up to date.
3. Always scan the files before transferring them to your USB.
4. Do not allow other users to use your PC i.e password protect it.
Subscribe to:
Posts (Atom)